CONTENTS
!!!笔记仅供学习交流使用,请勿进行其他用途!!!
kali:
dirb:
root@kali:~# dirb ----------------- DIRB v2.21 By The Dark Raver ----------------- ./dirb <url_base> [<wordlist_file(s)>] [options] ========================= NOTES ========================= <url_base> : Base URL to scan. (Use -resume for session resuming) <wordlist_file(s)> : List of wordfiles. (wordfile1,wordfile2,wordfile3...) ======================== HOTKEYS ======================== 'n' -> Go to next directory. 'q' -> Stop scan. (Saving state for resume) 'r' -> Remaining scan stats. ======================== OPTIONS ======================== -a <agent_string> : Specify your custom USER_AGENT. -c <cookie_string> : Set a cookie for the HTTP request. -f : Fine tunning of NOT_FOUND (404) detection. -H <header_string> : Add a custom header to the HTTP request. -i : Use case-insensitive search. -l : Print "Location" header when found. -N <nf_code>: Ignore responses with this HTTP code. -o <output_file> : Save output to disk. -p <proxy[:port]> : Use this proxy. (Default port is 1080) -P <proxy_username:proxy_password> : Proxy Authentication. -r : Don't search recursively. -R : Interactive recursion. (Asks for each directory) -S : Silent Mode. Don't show tested words. (For dumb terminals) -t : Don't force an ending '/' on URLs. -u <username:password> : HTTP Authentication. -v : Show also NOT_FOUND pages. -w : Don't stop on WARNING messages. -X <extensions> / -x <exts_file> : Append each word with this extensions. -z <milisecs> : Add a miliseconds delay to not cause excessive Flood. ======================== EXAMPLES ======================= ./dirb http://url/directory/ (Simple Test) ./dirb http://url/ -X .html (Test files with '.html' extension) ./dirb http://url/ /usr/share/dirb/wordlists/vulns/apache.txt (Test with apache.txt wordlist) ./dirb https://secure_url/ (Simple Test with SSL)
这里作者只是用最基本的方法,开始测试了一会就输入了【 q 】退出了。
root@kali:~# dirb http://cstriker1407.info
-----------------
DIRB v2.21
By The Dark Raver
-----------------
START_TIME: Tue May 6 21:04:37 2014
URL_BASE: http://cstriker1407.info/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4592
---- Scanning URL: http://cstriker1407.info/ ----
+ Dumping session state and Quitting.
-----------------
DOWNLOADED: 65 - FOUND: 0
dirbuster:
dirbuster是一个GUI版本的查找工具。使用界面如下,还是比较简单的,如下图:
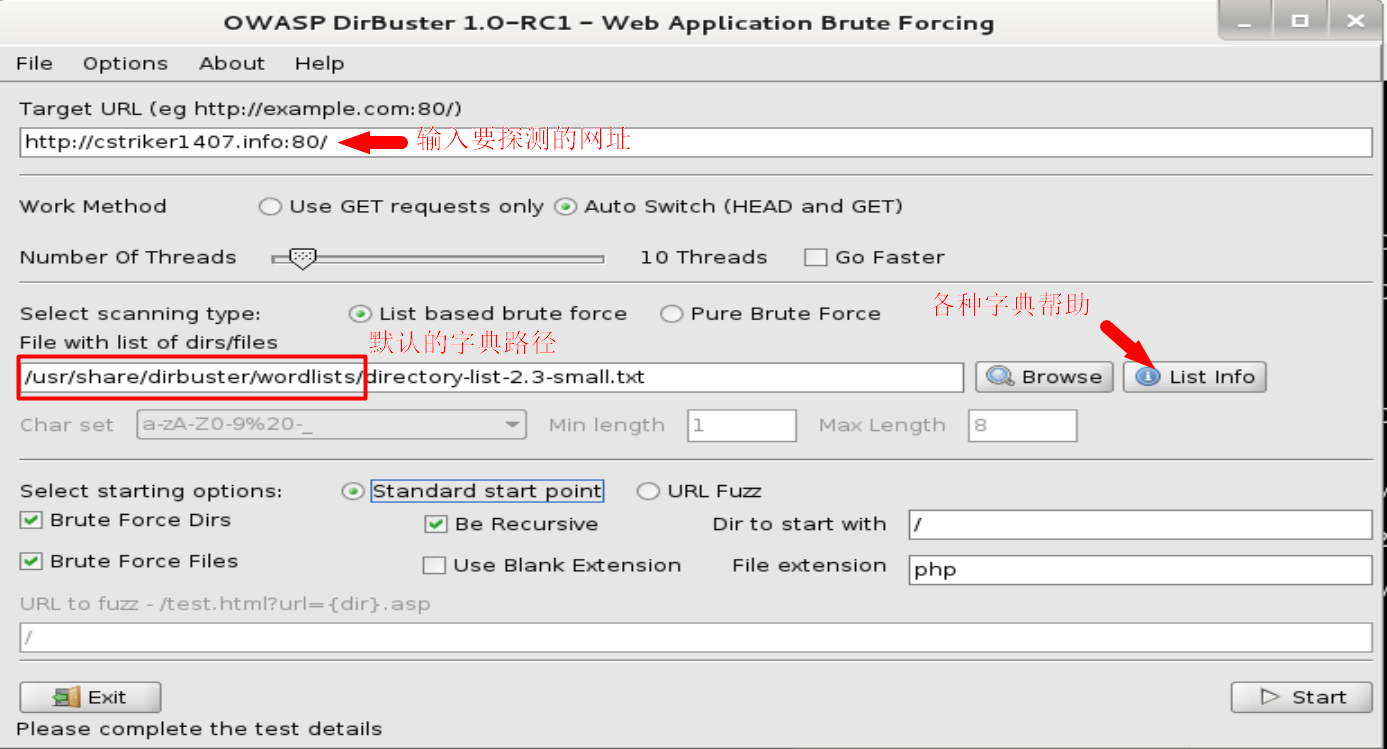
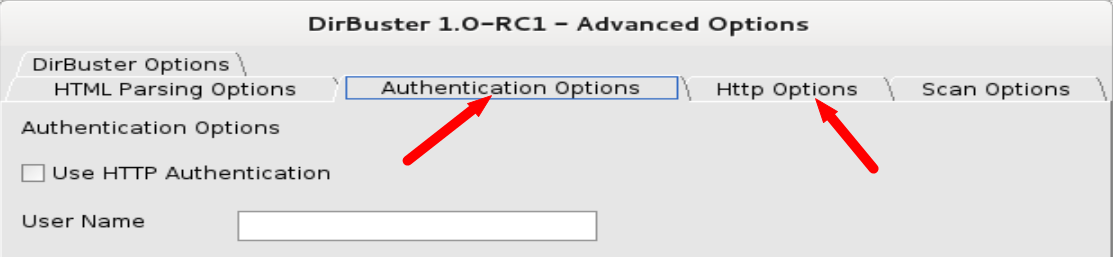
如果要设置用户名,密码或者http头等,可以进入高级选项设置,如下图:
metasploit:
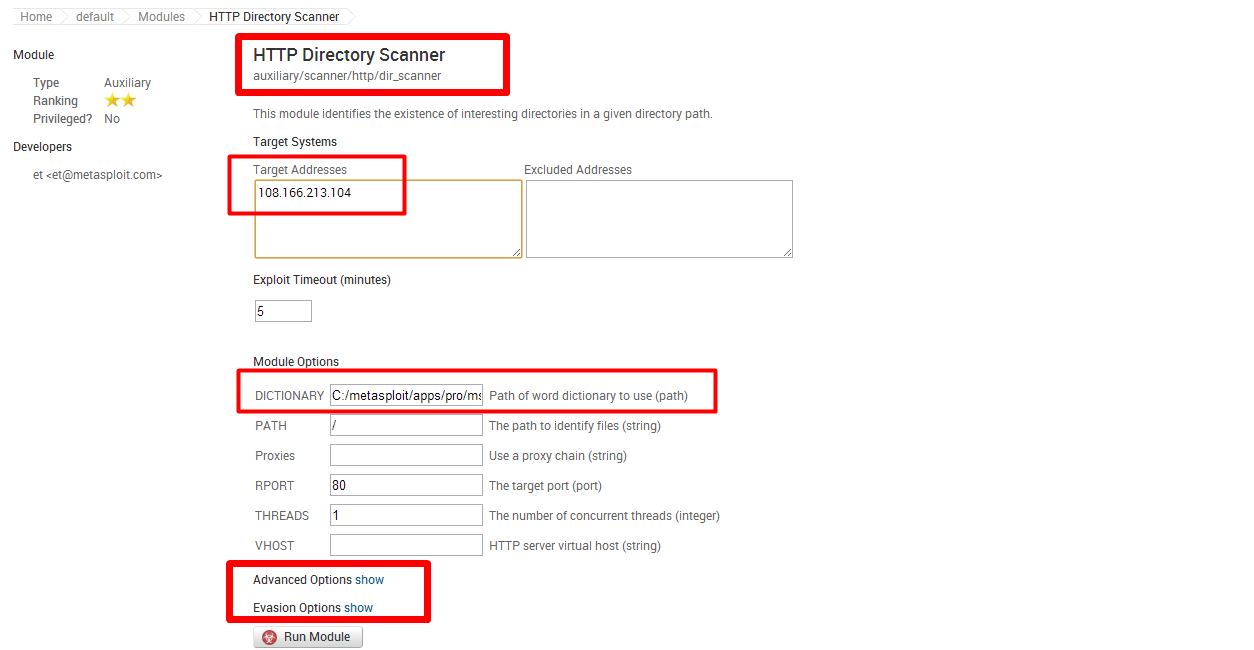
使用【 HTTP Directory Scanner 】模块:
msfconsole / kali:
root@kali:~# msfconsole msf > use auxiliary/scanner/http/dir_scanner msf auxiliary(dir_scanner) > show advanced ==>>可以查看高级选项 。。。。。。 。。。。。。 msf auxiliary(dir_scanner) > show evasion ==>>可以查看其他选项 。。。。。。 。。。。。。 msf auxiliary(dir_scanner) > show options ==>>常用选项 Module options (auxiliary/scanner/http/dir_scanner): Name Current Setting Required Description ---- --------------- -------- ----------- DICTIONARY /opt/metasploit/apps/pro/msf3/data/wmap/wmap_dirs.txt no Path of word dictionary to use PATH / yes The path to identify files Proxies no Use a proxy chain RHOSTS yes The target address range or CIDR identifier RPORT 80 yes The target port THREADS 1 yes The number of concurrent threads VHOST no HTTP server virtual host msf auxiliary(dir_scanner) > set RHOSTS 108.166.213.104 ==>>设置目标 RHOSTS => 108.166.213.104 msf auxiliary(dir_scanner) > cd /opt/metasploit/apps/pro/msf3/data/wmap/ ==>>可以看下都有哪些字典文件 msf auxiliary(dir_scanner) > ls [*] exec: ls whaler.txt wmap_404s.txt wmap_dirs.txt wmap_files.txt wmap_sample_profile.txt msf auxiliary(dir_scanner) > exploit ==>>开始测试
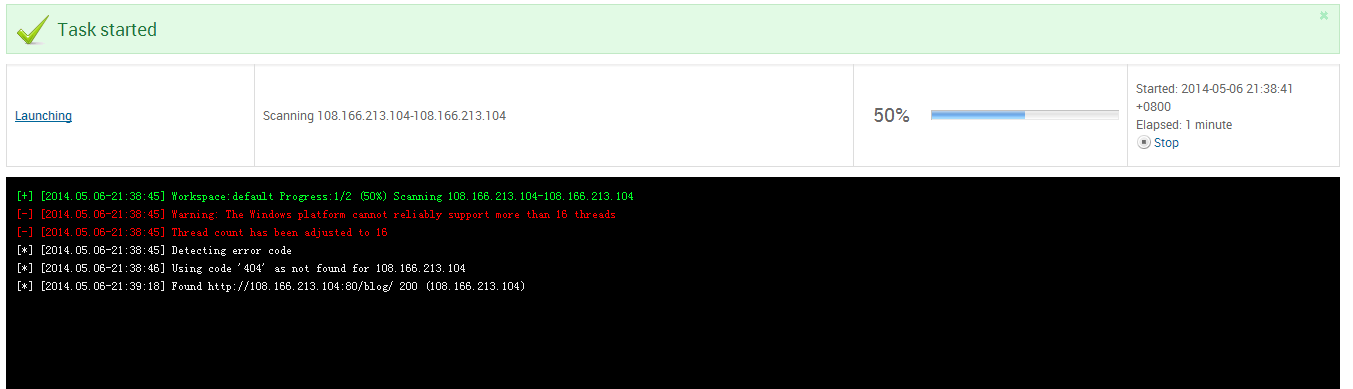
GUI / win7:
发表评论