!!!笔记仅供学习交流使用,请勿进行其他用途!!!
参考【 http://www.computersecuritystudent.com/SECURITY_TOOLS/DVWA/DVWAv107/lesson13/index.html 】
CONTENTS
nikto帮助文档
帮助文档比较复杂,这里就使用最简单的几种方法:
root@kali:~# nikto -H
Options:
-ask+ Whether to ask about submitting updates
yes Ask about each (default)
no Don't ask, don't send
auto Don't ask, just send
-Cgidirs+ Scan these CGI dirs: "none", "all", or values like "/cgi/ /cgi-a/"
-config+ Use this config file
-Display+ Turn on/off display outputs:
1 Show redirects
2 Show cookies received
3 Show all 200/OK responses
4 Show URLs which require authentication
D Debug output
E Display all HTTP errors
P Print progress to STDOUT
S Scrub output of IPs and hostnames
V Verbose output
-dbcheck Check database and other key files for syntax errors
-evasion+ Encoding technique:
1 Random URI encoding (non-UTF8)
2 Directory self-reference (/./)
3 Premature URL ending
4 Prepend long random string
5 Fake parameter
6 TAB as request spacer
7 Change the case of the URL
8 Use Windows directory separator (\)
A Use a carriage return (0x0d) as a request spacer
B Use binary value 0x0b as a request spacer
-Format+ Save file (-o) format:
csv Comma-separated-value
htm HTML Format
msf+ Log to Metasploit
nbe Nessus NBE format
txt Plain text
xml XML Format
(if not specified the format will be taken from the file extension passed to -output)
-Help Extended help information
-host+ Target host
-IgnoreCode Ignore Codes--treat as negative responses
-id+ Host authentication to use, format is id:pass or id:pass:realm
-key+ Client certificate key file
-list-plugins List all available plugins, perform no testing
-maxtime+ Maximum testing time per host
-mutate+ Guess additional file names:
1 Test all files with all root directories
2 Guess for password file names
3 Enumerate user names via Apache (/~user type requests)
4 Enumerate user names via cgiwrap (/cgi-bin/cgiwrap/~user type requests)
5 Attempt to brute force sub-domain names, assume that the host name is the parent domain
6 Attempt to guess directory names from the supplied dictionary file
-mutate-options Provide information for mutates
-nointeractive Disables interactive features
-nolookup Disables DNS lookups
-nossl Disables the use of SSL
-no404 Disables nikto attempting to guess a 404 page
-output+ Write output to this file ('.' for auto-name)
-Pause+ Pause between tests (seconds, integer or float)
-Plugins+ List of plugins to run (default: ALL)
-port+ Port to use (default 80)
-RSAcert+ Client certificate file
-root+ Prepend root value to all requests, format is /directory
-Save Save positive responses to this directory ('.' for auto-name)
-ssl Force ssl mode on port
-Tuning+ Scan tuning:
1 Interesting File / Seen in logs
2 Misconfiguration / Default File
3 Information Disclosure
4 Injection (XSS/Script/HTML)
5 Remote File Retrieval - Inside Web Root
6 Denial of Service
7 Remote File Retrieval - Server Wide
8 Command Execution / Remote Shell
9 SQL Injection
0 File Upload
a Authentication Bypass
b Software Identification
c Remote Source Inclusion
x Reverse Tuning Options (i.e., include all except specified)
-timeout+ Timeout for requests (default 10 seconds)
-Userdbs Load only user databases, not the standard databases
all Disable standard dbs and load only user dbs
tests Disable only db_tests and load udb_tests
-until Run until the specified time or duration
-update Update databases and plugins from CIRT.net
-useproxy Use the proxy defined in nikto.conf
-Version Print plugin and database versions
-vhost+ Virtual host (for Host header)
+ requires a value
nikto使用示例
使用前需要更新nikto,输入命令:
nikto -update
但有时候会出现网路问题,作者这里这样处理的,如下,不知道对不对。
root@kali:~# nikto -update + Retrieving 'db_tests' + ERROR: Unable to get CIRT.net/nikto/UPDATES/2.1.5/db_tests
首先查找文件【 db_tests 】:
root@kali:~# cd / root@kali:/# find . -name "db_tests" ./usr/share/webshag/database/nikto/db_tests ./var/lib/nikto/databases/db_tests
然后删掉文件,重新更新,就可以了:
root@kali:/# cd /var/lib/nikto/databases/ root@kali:/var/lib/nikto/databases# rm db_tests root@kali:/var/lib/nikto/databases# nikto -update + Retrieving 'db_tests' + CIRT.net message: Please submit Nikto bugs to http://trac2.assembla.com/Nikto_2/report/2
如果还是不行,就手动下载:
root@kali:/var/lib/nikto/databases# wget CIRT.net/nikto/UPDATES/2.1.5/db_tests
更新好之后就可以扫描了:
root@kali:/var/lib/nikto/databases# nikto -host http://192.168.168.109/DVWA-1.0.8 - Nikto v2.1.5 --------------------------------------------------------------------------- + Target IP: 192.168.168.109 + Target Hostname: 192.168.168.109 + Target Port: 80 + Start Time: 2014-04-28 23:08:40 (GMT8) --------------------------------------------------------------------------- + Server: Apache/2.4.9 (Unix) OpenSSL/1.0.1g PHP/5.5.11 mod_perl/2.0.8-dev Perl/v5.16.3 + Retrieved x-powered-by header: PHP/5.5.11 + The anti-clickjacking X-Frame-Options header is not present. + Cookie PHPSESSID created without the httponly flag + Cookie security created without the httponly flag + Root page / redirects to: login.php + No CGI Directories found (use '-C all' to force check all possible dirs) + Server leaks inodes via ETags, header found with file /DVWA-1.0.8/robots.txt, fields: 0x1a 0x4dba8594c3d80 + File/dir '/' in robots.txt returned a non-forbidden or redirect HTTP code (302) + "robots.txt" contains 1 entry which should be manually viewed. + Allowed HTTP Methods: POST, OPTIONS, GET, HEAD, TRACE + OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST + OSVDB-3268: /DVWA-1.0.8/config/: Directory indexing found. + /DVWA-1.0.8/config/: Configuration information may be available remotely. + OSVDB-3268: /DVWA-1.0.8/docs/: Directory indexing found. + /DVWA-1.0.8/login.php: Admin login page/section found. + 6545 items checked: 0 error(s) and 13 item(s) reported on remote host + End Time: 2014-04-28 23:09:03 (GMT8) (23 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
漏洞使用
877漏洞:
root@kali:/var/lib/nikto/databases# telnet 192.168.168.109 80 Trying 192.168.168.109... Connected to 192.168.168.109. Escape character is '^]'. get index.html 。。。。。。 。。。。。。 <a href="/">localhost</a><br /> <span>Apache/2.4.9 (Unix) OpenSSL/1.0.1g PHP/5.5.11 mod_perl/2.0.8-dev Perl/v5.16.3</span> </address> </body> </html> Connection closed by foreign host.
服务器的配置信息暴露了~~
3268漏洞:
查看网页:
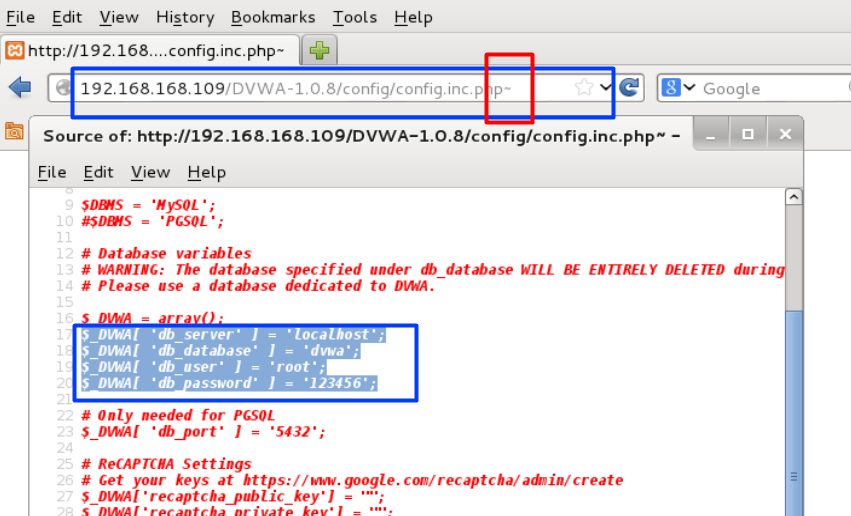
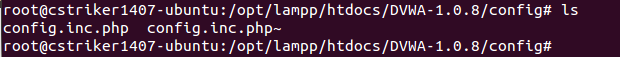
参看服务器端,果然有这个文件。
发表评论